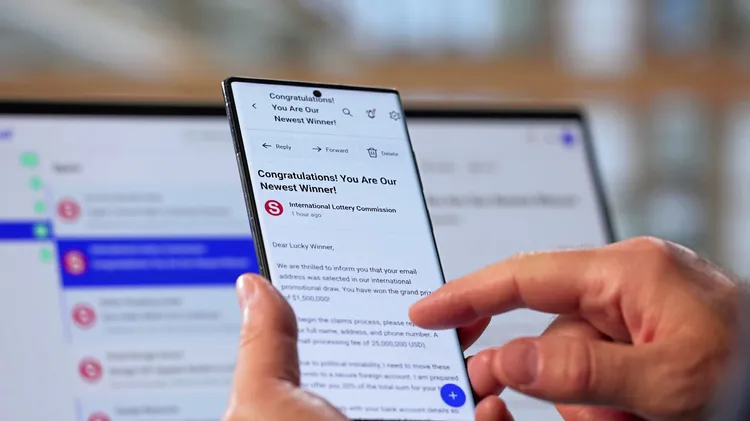
Forewarned is forearmed: Davey Winder explore
Get ready for the biggest security threats of 2025
10 min read
This article is from...
Read this article and 8000+ more magazines and newspapers on Readly